how to create(boot from) multiple operating system in 0ne pc(computer)
Lehvi
July 04, 2018
Computers normally have a single operating system installed on them, but you can dual-boot multiple operating systems. You can have two (or more) versions of Windows installed side-by-side on the same PC and choose between them at boot time.
Typically, you should install the newer operating system last. For example, if you want to dual-boot Windows 7 and 10, install Windows 7 and then install Windows 10 second. However, this may not always be necessary — installing Windows 7 after Windows 8 or 8.1 seems to work.
The Basics
The process for creating a dual-boot system is similar no matter what operating system you’re dual-booting with. Here’s what you’ll need to do:
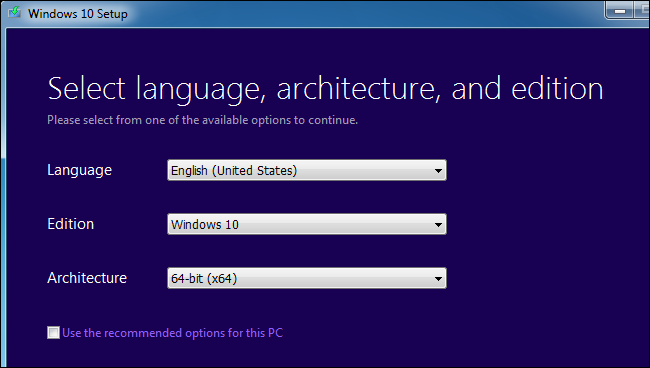
Install the First Version of Windows: If you already have a single Windows system installed on your computer, that’s fine. If not, install Windows normally. You may want to use custom partitioning settings and leave free space available on your hard drive for the second version of Windows.
Make Room For the Second Version of Windows: You’ll need available hard drive space for the next version of Windows. If you have Windows installed, you can resize the partition. You could also insert a second hard drive into your computer (if it’s a desktop computer) and install the second version of Windows to that hard drive.
Install the Second Version of Windows: Next, you’ll install the second version of Windows. Ensure you choose the “Custom Install” option, not the “Upgrade” option. Install it alongside the previous version of Windows, in a different partition on the same disk or on a different physical disk.
You’ll then be able to choose which copy of Windows you want to boot at boot time, and you can access the files from each version of Windows on the other one.
Install the First Version of Windows, If It’s Not Already Installed
Install the first version of Windows on your PC, assuming it’s not already installed. If your computer already has Windows installed on it, that’s fine. If you’re installing Windows fresh, you’ll want to choose the “Custom install” option when going through the installation wizard and create a smaller partition for Windows. Leave enough space for the other version of Windows. This means you won’t have to resize partitions later.
Shrink Your Windows Partition
You’ll now need to shrink your existing Windows partition to make room for the second copy of Windows. If you already have enough free space or you’re installing the second copy of Windows to a different hard disk entirely and it has available space, you can skip this.
Basically, this involves booting the existing Windows system on your computer and opening the Disk Management tool. (Do this by pressing Windows Key + R, typing diskmgmt.msc into the Run dialog, and pressing Enter.) Right-click the Windows partition and select the “Shrink Volume” option. Shrink it to make enough space for the other Windows system.
RELATED: How to Set Up BitLocker Encryption on Windows
If you’re using BitLocker encryption on your Windows system, you’ll first need to open the BitLocker Control Panel and click the “Suspend Protection” link next to the partition you want to resize. This will disable BitLocker encrpytion until you next reboot, and you’ll be able to resize the partition. Otherwise, you won’t be able to resize the partition.
Install the Second Version of Windows
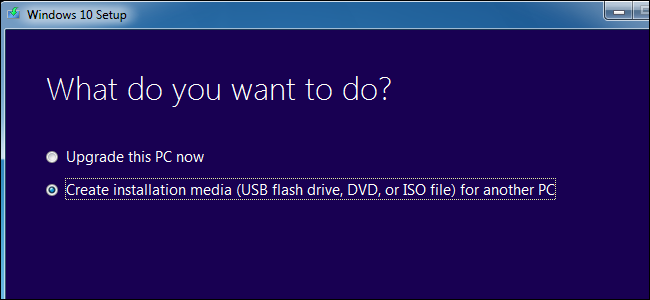
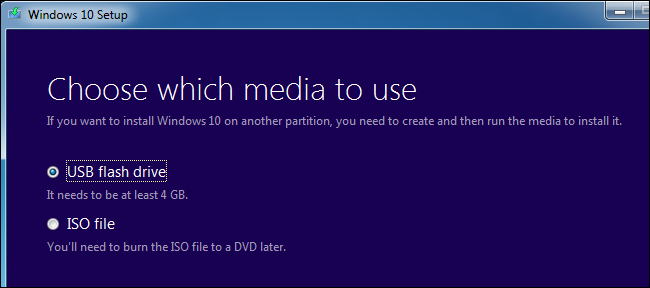
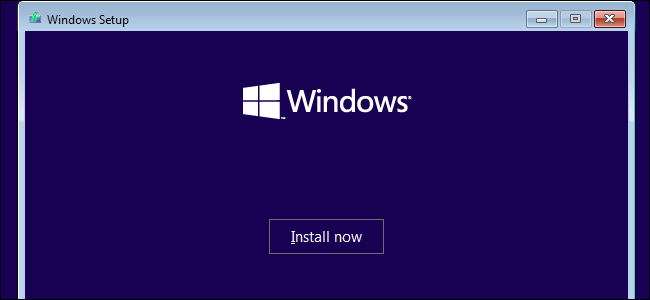
Next, insert the installation media for the second version of Windows you want to install and reboot your computer. Boot it and go through the installer normally. When you see the “Upgrade” or “Custom install” option, be sure to select “Custom” — if you select Upgrade, the second version of Windows will install over top of your first version of Windows.
Select the “unallocated space” and create a new partition on it. Tell Windows to install itself to this new partition. Just be sure not to select the partition containing the version of Windows currently installed on your system, as two versions of Windows can’t be installed on the same partition.
Windows will install normally, but it’ll install alongside the current version of Windows on your PC. Each version of Windows will be on a separate partition.
Choosing Your OS and Modifying Boot Settings
When the installation is finished, you’ll see a boot menu every time you boot your computer. Use this menu to select the version of Windows you want to boot.
Depending on which versions of Windows you’re using, the screen will look different. On Windows 8 and newer versions of Windows, it’s a blue screen with tiles with the title “Choose an operating system.” On Windows 7, it’s a black screen with a list of operating systems and the title “Windows Boot Manager.”
Either way, you can customize the boot menu’s settings from within Windows itself. Open the Control Panel, click the System and Security option, click the System icon, and click Advanced System Settings at the left side of the window. Select the Advanced tab and click the Settings button under Startup & Recovery. You can choose the default operating system that boots automatically and select how long you have until it boots.
If you want more operating systems installed, just install the additional operating systems on their own separate partitions.
Typically, you should install the newer operating system last. For example, if you want to dual-boot Windows 7 and 10, install Windows 7 and then install Windows 10 second. However, this may not always be necessary — installing Windows 7 after Windows 8 or 8.1 seems to work.
The Basics
The process for creating a dual-boot system is similar no matter what operating system you’re dual-booting with. Here’s what you’ll need to do:
Install the First Version of Windows: If you already have a single Windows system installed on your computer, that’s fine. If not, install Windows normally. You may want to use custom partitioning settings and leave free space available on your hard drive for the second version of Windows.
Make Room For the Second Version of Windows: You’ll need available hard drive space for the next version of Windows. If you have Windows installed, you can resize the partition. You could also insert a second hard drive into your computer (if it’s a desktop computer) and install the second version of Windows to that hard drive.
Install the Second Version of Windows: Next, you’ll install the second version of Windows. Ensure you choose the “Custom Install” option, not the “Upgrade” option. Install it alongside the previous version of Windows, in a different partition on the same disk or on a different physical disk.
You’ll then be able to choose which copy of Windows you want to boot at boot time, and you can access the files from each version of Windows on the other one.
Install the First Version of Windows, If It’s Not Already Installed
Install the first version of Windows on your PC, assuming it’s not already installed. If your computer already has Windows installed on it, that’s fine. If you’re installing Windows fresh, you’ll want to choose the “Custom install” option when going through the installation wizard and create a smaller partition for Windows. Leave enough space for the other version of Windows. This means you won’t have to resize partitions later.
Shrink Your Windows Partition
You’ll now need to shrink your existing Windows partition to make room for the second copy of Windows. If you already have enough free space or you’re installing the second copy of Windows to a different hard disk entirely and it has available space, you can skip this.
Basically, this involves booting the existing Windows system on your computer and opening the Disk Management tool. (Do this by pressing Windows Key + R, typing diskmgmt.msc into the Run dialog, and pressing Enter.) Right-click the Windows partition and select the “Shrink Volume” option. Shrink it to make enough space for the other Windows system.
RELATED: How to Set Up BitLocker Encryption on Windows
If you’re using BitLocker encryption on your Windows system, you’ll first need to open the BitLocker Control Panel and click the “Suspend Protection” link next to the partition you want to resize. This will disable BitLocker encrpytion until you next reboot, and you’ll be able to resize the partition. Otherwise, you won’t be able to resize the partition.
Install the Second Version of Windows
Next, insert the installation media for the second version of Windows you want to install and reboot your computer. Boot it and go through the installer normally. When you see the “Upgrade” or “Custom install” option, be sure to select “Custom” — if you select Upgrade, the second version of Windows will install over top of your first version of Windows.
Select the “unallocated space” and create a new partition on it. Tell Windows to install itself to this new partition. Just be sure not to select the partition containing the version of Windows currently installed on your system, as two versions of Windows can’t be installed on the same partition.
Windows will install normally, but it’ll install alongside the current version of Windows on your PC. Each version of Windows will be on a separate partition.
Choosing Your OS and Modifying Boot Settings
When the installation is finished, you’ll see a boot menu every time you boot your computer. Use this menu to select the version of Windows you want to boot.
Depending on which versions of Windows you’re using, the screen will look different. On Windows 8 and newer versions of Windows, it’s a blue screen with tiles with the title “Choose an operating system.” On Windows 7, it’s a black screen with a list of operating systems and the title “Windows Boot Manager.”
Either way, you can customize the boot menu’s settings from within Windows itself. Open the Control Panel, click the System and Security option, click the System icon, and click Advanced System Settings at the left side of the window. Select the Advanced tab and click the Settings button under Startup & Recovery. You can choose the default operating system that boots automatically and select how long you have until it boots.
If you want more operating systems installed, just install the additional operating systems on their own separate partitions.
how to create(boot from) multiple operating system in 0ne pc(computer)
![how to create(boot from) multiple operating system in 0ne pc(computer)]() Reviewed by Lehvi
on
July 04, 2018
Rating:
Reviewed by Lehvi
on
July 04, 2018
Rating: